 Within 3 days, two Anti-Virus (Kaspersky & Bitdefender) websites were reported being hacked. Sensitive information such as Users info, account password were claim to be havested. Both attacks were reported to be using simple SQL injection on their databases.
Within 3 days, two Anti-Virus (Kaspersky & Bitdefender) websites were reported being hacked. Sensitive information such as Users info, account password were claim to be havested. Both attacks were reported to be using simple SQL injection on their databases.Kaspersky
The hacker posted in the blog, claiming that just by altering one of the parameters, he was able to access every field in the database such as users, activation codes, lists of bugs, admins, shop, etc. So far, representatives from Kaspersky declined to comment on the vulnerbility.
The picture shows the version, username and name of the database. The other shows username, host and password for mysql user.

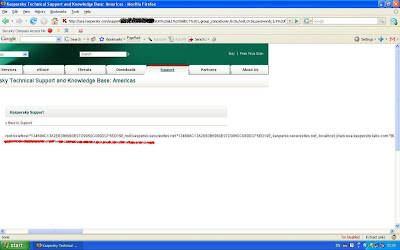
Updated on 15 Feb 09
An independent auditor has reported that no customer information was exposed during last week breach on the Kaspersky website, after an internal investigation conducted by the firm.
It wasn't the first time that a Kaspersky site was hit by a SQL injection attack. In July last year, Kaspersky's Malaysian site was defaced by hacker who left pro-Turkish slogans "hacked by m0sted And Amen Kaspersky Shop Hax0red No War Turkish Hacker Thanx to Terrorist Crew all team members".

Bitdefender
Bitdefender's portugese also been hit by SQL injection attack on their database. Customer sensitive data were extracted. It was said that "bitdefender.pt" is hosted by a reseller for bitdefender.
The picture shows the version, username and name of the database. The other shows the Admin userName, userPass, sessionID and lastlog.
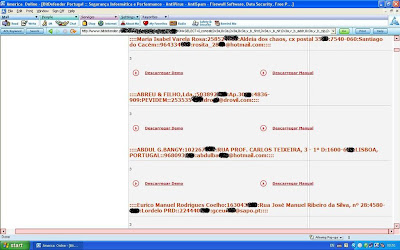
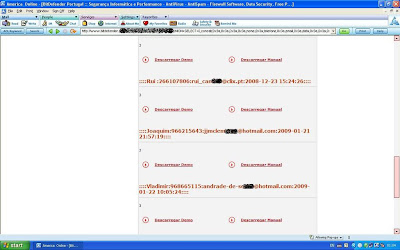
The attack extracts details of the customers and sales table (tabel vendas). Under the table inscricoes(Newsletter), there are thousands of email addresses that can be useful for spammer.


Related Reports:
- SecurityFocus: Kaspersky exposes sensitive database, says hacker
- ZDnet.com: Kaspersky’s Malaysian site hacked by Turkish hacker
- HackerBlog: Bitdefender (Portugal) exposes sensitive customer data
Updated Report
- Kaspersky breach: No user info lifted, auditor confirms

1 comment:
After Kaspersky and BitDefender, it’s found that F-Secure.com also vulnerable to SQL Injection plus Cross Site Scripting. Fortunately, F-Secure doesn’t leak sensitive data, just some statistics regarding past virus activity.
Post a Comment